Cybersecurity is the practice of protecting systems, networks, and data from malicious attacks. As technology evolves, so do the methods used by cybercriminals. Understanding the landscape is essential for everyone.
With the rise of digital platforms, the importance of cybersecurity has increased dramatically. Individuals and organizations must prioritize cyber safety to safeguard sensitive information. This article explores various aspects of cybersecurity.
Master Cybersecurity with Kaspersky Premium
Kaspersky Premium offers advanced protection against evolving cyber threats. It combines state-of-the-art technology with user-friendly interfaces. This ensures that even non-technical users can defend their digital lives effectively.
Using Kaspersky Premium, you can benefit from real-time threat detection and automatic updates. This keeps your system secure against the latest malware and vulnerabilities. Investing in robust security software is crucial for peace of mind.
The Scale of the Cyber Threat
The scale of the cyber threat is vast and continuously growing. In recent years, data breaches have exposed millions of records. The financial and reputational impact on organizations can be devastating.
Cybercriminals target various sectors, including healthcare, finance, and retail. These industries often hold valuable personal and financial data. Thus, understanding this threat landscape is critical for effective cybersecurity measures.
Types of Cyber Threats
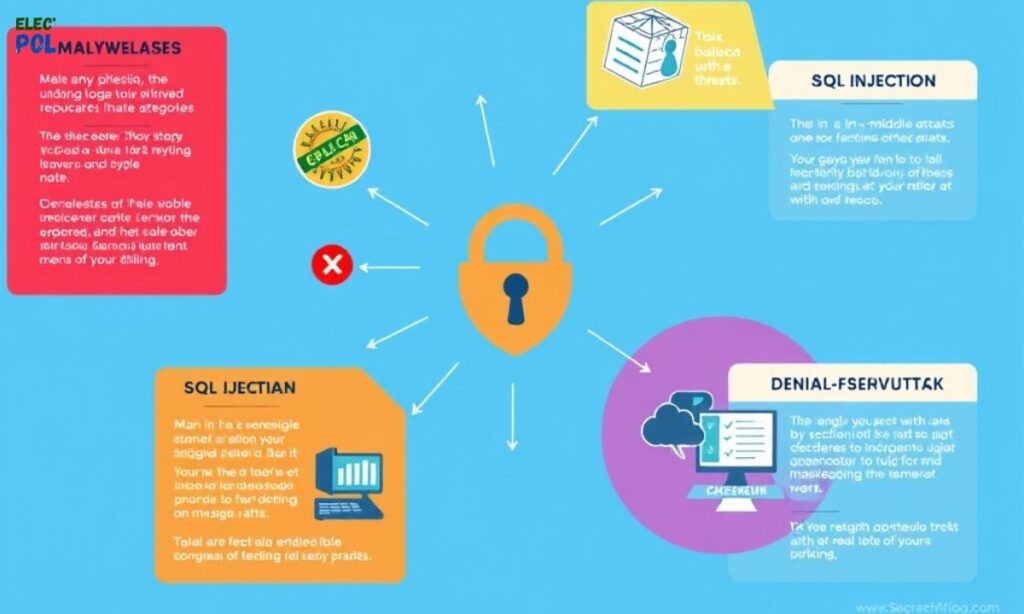
Understanding the types of cyber threats is essential to building a robust defense. Common threats include malware, phishing, and denial-of-service attacks. Each type poses unique risks that require tailored responses.
Awareness of these threats can significantly reduce the likelihood of a successful attack. Organizations and individuals must implement strategies to combat these risks effectively.
Malware
Malware is malicious software designed to disrupt, damage, or gain unauthorized access to systems. It can take various forms, such as viruses, Trojans, and ransomware. Each type of malware has its own methods of infection and damage.
Protecting against malware requires comprehensive security measures. Regularly updating software and using reliable antivirus programs can mitigate risks. Awareness and education are also vital in preventing malware infections.
SQL Injection
SQL injection is a type of cyber-attack that targets databases. Cybercriminals exploit vulnerabilities in applications to execute malicious SQL statements. This can lead to unauthorized access to sensitive data.
To prevent SQL injection attacks, developers must validate user inputs. Implementing security best practices during application development is crucial. Regular security audits can also help identify potential vulnerabilities.
Read this Blog: What is VPN? How It Works, Types of VPN
Phishing
Phishing attacks involve tricking individuals into revealing sensitive information. Cybercriminals send emails that appear legitimate, asking for personal data. These attacks can lead to identity theft and financial loss.
To protect against phishing, users should verify email sources before clicking links. Training staff on recognizing phishing attempts is essential for organizations. Awareness can significantly reduce the success rate of these attacks.
Man-in-the-Middle Attack
A man-in-the-middle attack occurs when an attacker intercepts communication between two parties. This can happen on unsecured networks, compromising sensitive data. The attacker can access private information without either party’s knowledge.
Using secure connections, such as VPNs, can help prevent these attacks. Educating users about the risks of public Wi-Fi is also important. Awareness and vigilance can reduce the likelihood of falling victim to this threat.
Denial-of-Service Attack
A denial-of-service (DoS) attack overwhelms systems, rendering them unusable. Cybercriminals flood networks with traffic, preventing legitimate access. This can halt operations and cause significant financial losses.
Protecting against DoS attacks requires robust network security measures. Organizations should implement traffic monitoring and filtering systems. Preparedness and incident response plans are vital for mitigating risks.
Latest Cyber Threats

Staying informed about the latest cyber threats is crucial for effective defense. New threats emerge regularly, requiring constant vigilance. Organizations must adapt their strategies to address these evolving risks.
Recent threats, such as Dridex malware and romance scams, highlight the need for continuous education. Understanding these threats can help individuals and businesses protect their data.
Dridex Malware
Dridex malware is a financial Trojan that primarily targets banking information. It spreads through phishing emails, compromising systems and stealing sensitive data. The financial impact of Dridex can be severe for affected organizations.
To combat Dridex, users should maintain updated antivirus software. Regularly reviewing financial statements can help detect unauthorized transactions. Being proactive is essential for reducing the risk of infection.
Romance Scams
Romance scams exploit emotional vulnerabilities to defraud victims. Cybercriminals create fake identities to establish relationships and solicit money. These scams can lead to significant financial losses for individuals.
Awareness is key in preventing romance scams. Users should be cautious when sharing personal information online. Reporting suspicious activities can also help authorities combat these scams effectively.
Read This Blog: What is Cryptocurrency and How Does It Work?
Emotet Malware
Emotet is a sophisticated malware strain that can steal data and distribute other malware. It often spreads through malicious email attachments. The evolving nature of Emotet makes it a persistent threat.
To protect against Emotet, users should avoid opening suspicious emails. Employing advanced security solutions can also help detect and block this malware. Regularly updating systems is vital for maintaining security.
End-User Protection
End-user protection is critical for maintaining cybersecurity. Often, individuals inadvertently contribute to security breaches. Educating users about safe practices can significantly enhance overall security.
Employing endpoint protection solutions can help monitor and secure devices. Organizations should prioritize user training to reduce the risk of human error. A proactive approach is essential for effective cybersecurity.
Cyber Safety Tips – Protect Yourself Against Cyberattacks

Update Software: Regularly update your operating system and applications to patch vulnerabilities.
Use Antivirus Software: Invest in reputable antivirus software and keep it up to date.
Create Strong Passwords: Use complex passwords that are difficult to guess and change them regularly.
Be Cautious with Emails: Do not open attachments or click links from unknown senders.
Avoid Unsecured Networks: Be wary of using public Wi-Fi networks, especially for sensitive transactions.
Frequently Asked Questions
What is cybersecurity?
Cybersecurity involves protecting systems and networks from digital attacks, ensuring data integrity and privacy.
Why is cybersecurity important?
Cybersecurity is crucial for safeguarding sensitive information and maintaining trust in digital transactions.
What are common types of cyber threats?
Common threats include malware, phishing, SQL injection, and denial-of-service attacks.
How can individuals protect themselves online?
Individuals can protect themselves by using strong passwords, avoiding suspicious emails, and keeping software updated.
What role does end-user education play in cybersecurity?
End-user education is vital for preventing human error, which is a common vulnerability in cybersecurity.
Conclusion
In conclusion, cybersecurity is a vital aspect of modern life. Understanding the types of threats and implementing safety measures can significantly reduce risks. By prioritizing cybersecurity, individuals and organizations can protect their sensitive information and enhance their digital safety.

I’m passionate electric scooter enthusiast and the voice behind this blog. I’m here to share my expertise and insights with you. From in-depth reviews to problem-solving guides, my goal is to help you make the most of your electric scooter experience.








![Gomyfinance.com Invest: I Made $5,000 in My First Month [Real Results 2025]](https://electopolo.com/wp-content/uploads/2025/05/Gomyfinance.com-Invest-I-Made-5000-in-My-First-Month-Real-Results-2025-150x150.jpg)


